In this article, we will install the ADFS in Azure VM.
Prerequisites:
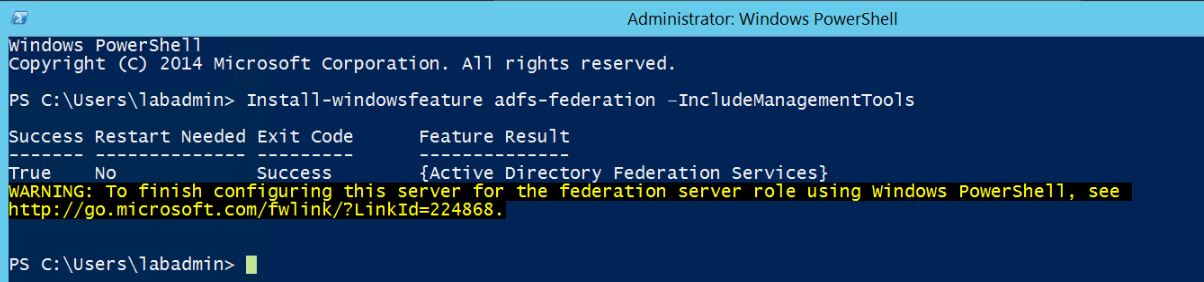
Install-windowsfeature adfs-federation –IncludeManagementTools
Step 2 Create a certificate request.
In the lab, I am using the LetsEncrypt free cert so I will skip the steps. if you would like to see how I
got this cert, please check out my this post.
Step 3) Add KDS Root key
Enable gMSA in your domain by running the following Windows PowerShell command on a domain controller, which runs Windows Server 2012 or later.
Add-KdsRootKey –EffectiveTime (Get-Date).AddHours(-10)
Step 4) Configure the first federation server in a new federation server farm
Open the Server Manager, and click on "Configure the federation service on this Server"
that should open the below dialogue box, hit next.
specify the account details.
Import the certificate we exported in (.pfx) format in the previous step, and provide the "Federation Service Display Name"
Provide the service account details.
Continue with the default selection.
review the selection and click next.
If all the Pre-requisite checks are pass click on "Configure" to continue.
you should the screen like below after a successful configuration.
Next, let's test the ADFS.
Note: Before we can test, make sure you have DNS record set up so that URL "sts.lab365.in" is resolvable and can reach the ADFS server, also for the service to be available externally, open the port 443 in the firewall, and publish CNAME record in the DNS, in my Azure LAB "sts.lab365.in" point to my VM external URL which would be like "adfs01.westindia.cloudapp.azure.com".
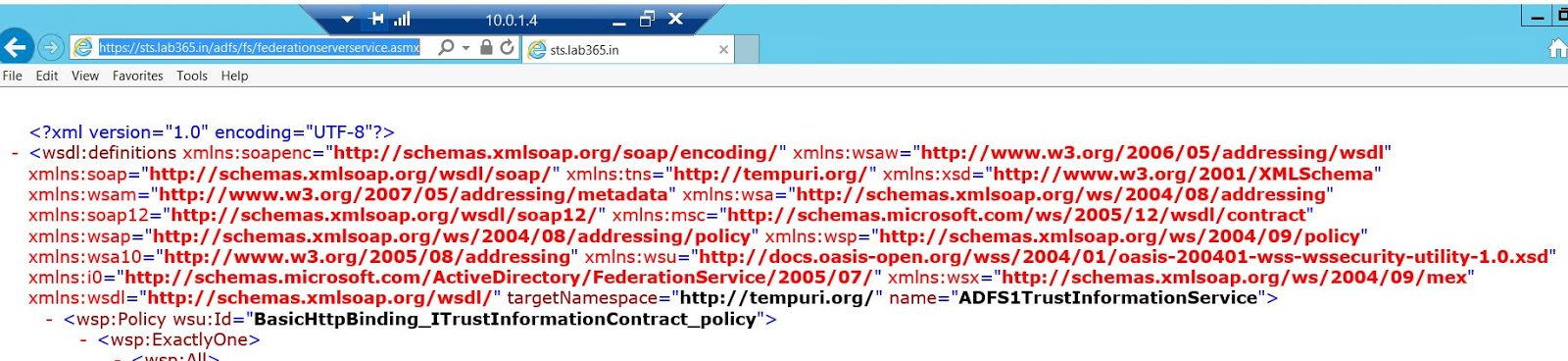
Once all the DNS records are setup we can use the below URL, which should return the XML.
https://sts.lab365.in/adfs/fs/federationserverservice.asmx
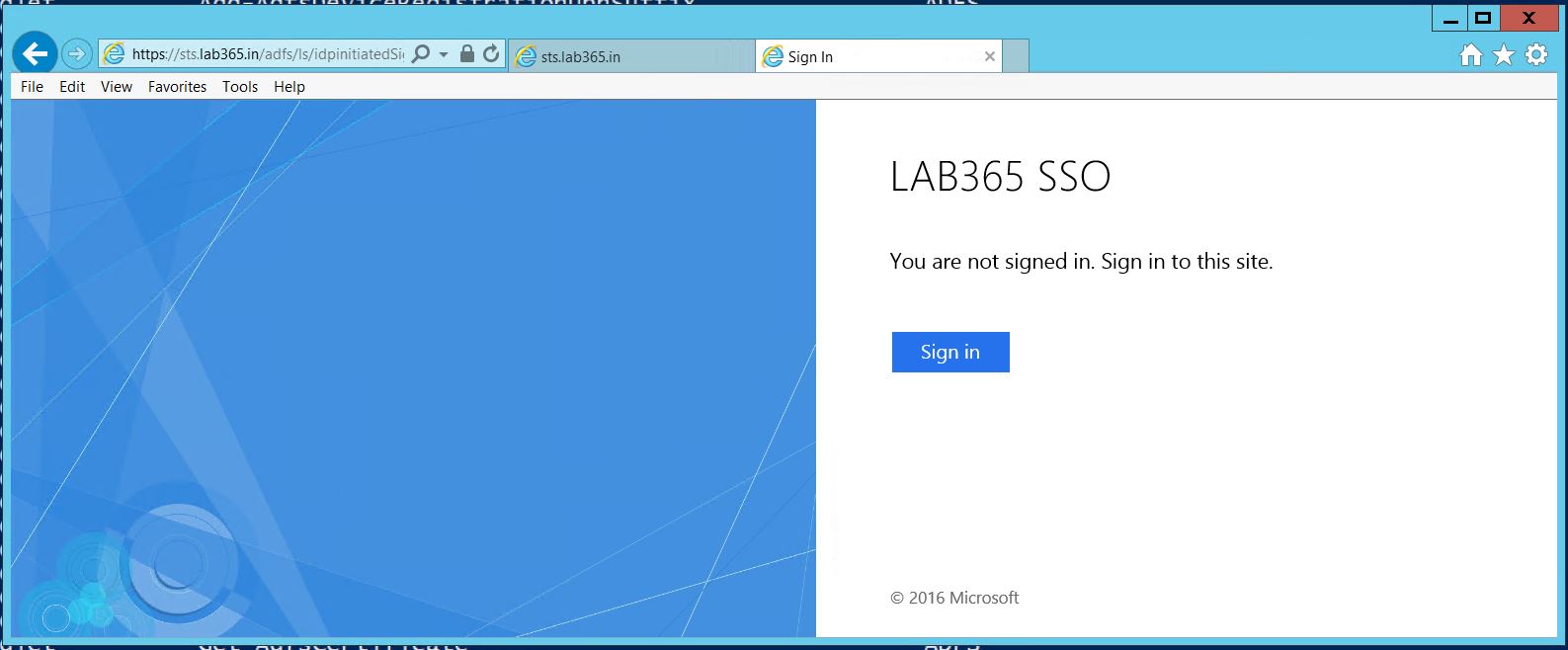
Also, check the LDAP Signon page URL if it's working.
https://ADFS_FQDN/adfs/ls/idpinitiatedSignOn.aspx
Note that you need the enable it before testing, as its disabled by default.
Set-AdfsProperties –EnableIdpInitiatedSignonPage $True
Step 5) - Configure Federation Trust with Office 365
Connect to MSOL Service and run the following cmd.
Prerequisites:
- Create a Service Account with Domain/Enterprise Admin rights
- Cloud only account with Global Admin rights
- Third-party SSL certificate
- AAD Connect (Directory Sync)
- Install ADFS Server
- Import Certificate and complete the Setup
- Post Install testing
- Setting up DNS record and open firewall port
- Convert domain to federated
- Test the working of the ADFS.
Step 1 - Install the ADFS server, join the server to the domain and reboot.

Step 2 Create a certificate request.
In the lab, I am using the LetsEncrypt free cert so I will skip the steps. if you would like to see how I
got this cert, please check out my this post.
Step 3) Add KDS Root key
Enable gMSA in your domain by running the following Windows PowerShell command on a domain controller, which runs Windows Server 2012 or later.
Add-KdsRootKey –EffectiveTime (Get-Date).AddHours(-10)
Step 4) Configure the first federation server in a new federation server farm
Open the Server Manager, and click on "Configure the federation service on this Server"
that should open the below dialogue box, hit next.
specify the account details.
Import the certificate we exported in (.pfx) format in the previous step, and provide the "Federation Service Display Name"
Provide the service account details.
Continue with the default selection.
review the selection and click next.
If all the Pre-requisite checks are pass click on "Configure" to continue.
you should the screen like below after a successful configuration.
Next, let's test the ADFS.
Note: Before we can test, make sure you have DNS record set up so that URL "sts.lab365.in" is resolvable and can reach the ADFS server, also for the service to be available externally, open the port 443 in the firewall, and publish CNAME record in the DNS, in my Azure LAB "sts.lab365.in" point to my VM external URL which would be like "adfs01.westindia.cloudapp.azure.com".
Once all the DNS records are setup we can use the below URL, which should return the XML.
https://sts.lab365.in/adfs/fs/federationserverservice.asmx

Also, check the LDAP Signon page URL if it's working.
https://ADFS_FQDN/adfs/ls/idpinitiatedSignOn.aspx
Note that you need the enable it before testing, as its disabled by default.
Set-AdfsProperties –EnableIdpInitiatedSignonPage $True
Step 5) - Configure Federation Trust with Office 365
Connect to MSOL Service and run the following cmd.
Connect-MsolService
Set-MsolADFSContext –computer adfs02.lab365.in
Convert-MsolDomainToFederated –domain lab365.in
Step 6) - Sync local Active Directory user accounts to Office 365
Now run the AD Connect sync if not already run and the users should now be redirected to ADFS for authentication.
This completes my post in setting up ADFS on Azure VM, where we successfully installed, configured and tested the ADFS.
Set-MsolADFSContext –computer adfs02.lab365.in
Convert-MsolDomainToFederated –domain lab365.in
Step 6) - Sync local Active Directory user accounts to Office 365
Now run the AD Connect sync if not already run and the users should now be redirected to ADFS for authentication.
This completes my post in setting up ADFS on Azure VM, where we successfully installed, configured and tested the ADFS.










Comments
Post a Comment